Introduction
In early 2014 Edward Snowden revealed that British intelligence services had been collecting webcam images sent by Yahoo Messenger users worldwide.
Yahoo Messenger has two features which employ a webcam:
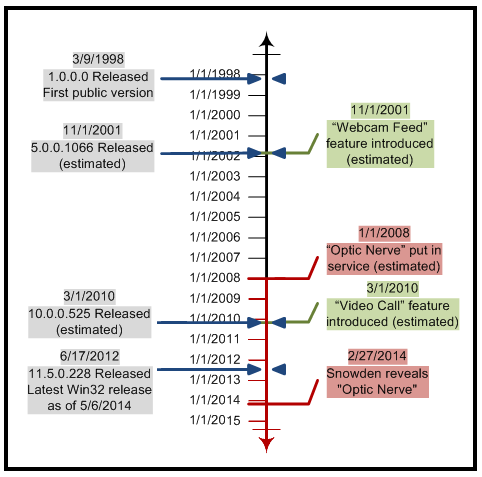
- "Webcam Feed" (my term). Available since v5.0.0.1066 (Nov 2001). Users can "invite" others to view their webcam. Audio is not transmitted.
- "Video Chat". Available since v10.0.0.525 (Mar 2010). Users can make a "Video Call" to converse with live video and audio.
We'll discuss feature #2 at another time.
For now, let's take a look at feature #1 and how NSA/GCHQ might have extracted images from packet captures.
Background
The report by the Guardian indicates that the GCHQ program named Optic Nerve was active from sometime in 2008 until at least sometime in 2012.
I've been trying to break instant messenger clients since resource-editing AOL Instant Messenger's rich text editor component in the late nineties, so I was naturally curious about how difficult it was to do this.
Laboratory set-up
Here's how I configured my lab:
- Downloaded Yahoo Messenger client v9.0.0.2018 (released Oct 2008), on a hunch that it was vulnerable.
- Installed the client on two Windows XP VirtualBox Virtual Machines: "VM1" and "VM2" with bridged-mode networking on two separate host machines. I had no luck configuring the ActiveX image capture stack nor the "devenum" trick in WINE.
- Created two Yahoo accounts via the client's GUI.
- Installed SplitCam v6.6.41, a "webcam emulator", on both VMs. I didn't want to muck around with Host->Guest USB pass-through to use physical webcams.
Capturing packets
Next I captured the packets sent between clients while using the webcam feed feature. See Appendix A for some screenshots of the clients.
- Downloaded the first two small AVI files (1, 2) I could find on the web and configured SplitCam to use each as a video source on VM1 and VM2 respectively.
- Started a Wireshark packet capture on the host of VM1.
- Logged in on both clients using my two new Yahoo accounts.
- Chose "Invite user to view my webcam" on VM1.
- Accepted request on VM2.
- Chose "Invite user to view my webcam" on VM2.
- Accepted request on VM1.
- Waited about 10 seconds for some image frames to be transferred.
- Stopped and saved the packet capture in "Wireshark/tcpdump/..." pcap format (not pcapng).
Here's the resulting 400KB packet capture.
By law in the USA, you need permission to capture packets on a networks you don't own. I've only used this tool on my test network. Please see the LICENSE file for additional disclaimers.
Locating image data
A quick inspection of the capture in Wireshark, confirmed by an "Endpoints" Analysis, revealed that many TCP packets were sent from port 5100 on each machine.
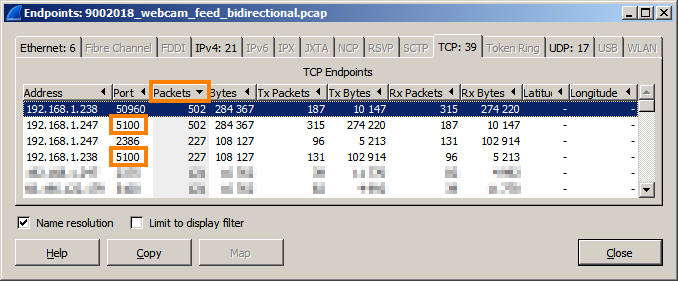
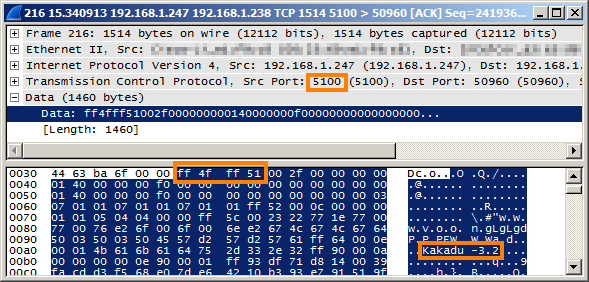
Many of these packets contained the string Kadadu-3.2. Searching the web turned up Kakadu Software - creators of "the world's leading JPEG2000 developer toolkit".
Sure enough the first 4 bytes of these packets, ff 4f ff 51, is the "magic" sequence for an "unwrapped" JPEG2000 "code stream". I confirmed this with "Export selected packet bytes" and the file(1) utility.
I found that IrfanView v4.37 for Windows can display JPEG200 codestreams, but didn't immediately find an option for Linux.
Automating image extraction
Let's write a script that will extract these codestreams and save them to disk as PNGs.
Many tools exist to "carve" files from a packet capture based on signatures: NetworkMiner, Ettercap, flowgrep, Xplico, Driftnet, Wireshark with a dissector, tcpxtract, and others. I wrote one from scratch in Python for a few reasons:
- To support multiple platforms - I've tested the script on Windows XP SP3, Ubuntu 13.10, and openSUSE 13.1.
- For a learning experience - I wanted to try capturing from a "live" interface in addition to reading a packet capture from disk.
- Other tools weren't easily extensible - we need to call a codestream->PNG conversion utility for each image extracted.
The script uses the dpkt library from Dug Song and Jon Oberheide to parse ethernet frames and the Glymur library to process JPEG2000 data.
You can view the script with syntax highlighting here and download it here.
If you're really impatient, I've created a virtual machine with all necessary libraries installed. The script and the .pcap file from above are in /root. Use 'root'/'linux' to log in. Here are 350MB compressed(1GB uncompressed) VMX/VMDK and OVF images tested with VMWare Player v6.0.2 build-1744117 and Virtualbox 4.2.16_Ubuntu r86992 respectively. This is the SUSE Studio configuration used to create the above images.
OK. Back to the script...
$ ./optic_nerve_yahoo_capture.py --help
usage: optic_nerve_yahoo_capture.py [-h] [-i NETWORK_INTERFACE] [-f PCAPFILE]
Extracts JPEG 2000 Yahoo Messenger webcam images from given pcap file or given
network interface and writes them to the current directory as PNG images named
in this form: PKTNUM-SRCIP-DSTIP-YYYYMMDD-HHMMSS.bmp where PKTNUM is the
packet number from the capture/interface, SRCIP is the source IP address,
DSTIP is the destination IP address, and YYYYMMDD-HHMMSS is the time and date
the image was captured.
optional arguments:
-h, --help show this help message and exit
Input:
-i NETWORK_INTERFACE Network interface to sniff packets from (e.g. 'wlan0')
-f PCAPFILE PCAP file to read packets from (e.g. 'foo.pcap')
Here's what you'll see if you feed it the .pcap file provided in "Capturing packets" above:
$ ./optic_nerve_yahoo_capture.py -f 9002018_webcam_feed_bidirectional_only_5100.pcap
[...]
encountered potential yahoo messenger webcam feed data in packet number 26
pkt_timestamp: 1400251938.79 pkt_src: 192.168.1.247 pkt_dst: 192.168.1.238
data: ff:4f:ff:51:00:2f:00:00:00:00:01:40:00:00:00:f0:00:00:00:00 +[...]
encountered beginning of new codestream
writing previous codestream (size 4160 ) to /tmp/tmpuRR3dO.jpc
wrapping previous codestream and writing it to /tmp/tmpfWKGPG.jp2
writing PNG to 26-192.168.1.247-192.168.1.238-20140516_105218.png
encountered potential yahoo messenger webcam feed data in packet number 27
[...]
Extracted and converted images are written to the current directory:
$ ls
total 8972
100-192.168.1.247-192.168.1.238-20140516_105223.png
109-192.168.1.247-192.168.1.238-20140516_105223.png
114-192.168.1.247-192.168.1.238-20140516_105224.png
120-192.168.1.247-192.168.1.238-20140516_105224.png
126-192.168.1.247-192.168.1.238-20140516_105225.png
[...]
Vulnerability timeline
As of 5/6/2014, the most recent Windows version of Yahoo Messenger doesn't encrypt webcam feeds. See Appendix B for more details on past versions.
Note that Yahoo also offers clients for Mac, iPhone, and Android.
Appendix A - Yahoo Messenger v9.0.2018 Screenshots
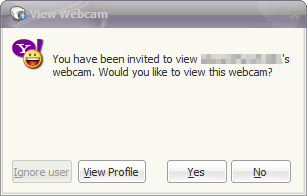
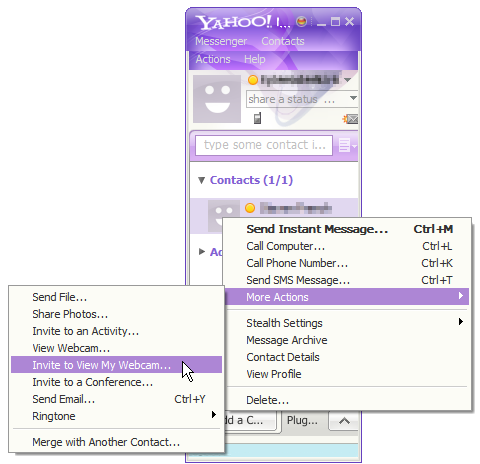
Appendix B - Historic versions of the Yahoo Messenger client
I have mirrored all the above installers in this Google drive folder. Most of them were originally retrieved from Oldversion.com.
comments powered by Disqus